About
Offensive Security Solutions
Know the Unknown and Understand the Consequences!
Many organizations get breached despite having good cyber defense tools & processes. The cyber security market is flooded with technical solutions for cyber defense and every year there is a better version coming in market, but yet the breaches are on rise. Why?
How do you know the cyber defense you have put in place inside your environment is good enough to protect you from modern day cyber- attacks?
With our offensive testing services, get unprecedented visibility into your web apps, infrastructure, Wi-Fi, mobile apps, containers, cloud and in-house built applications. Valuesec security professionals simulate the behaviour of a sophisticated attacker to identify complex vulnerabilities. We resolve discovered flaws and provide solutions for long-term best practices.
Rely on our comprehensive suite of offensive security services to assess, identify, illuminate, hunt, protect, mitigate and strengthen your capabilities to multidimensional threats across whole IT and business landscape of your organization.
Summary of our Approach
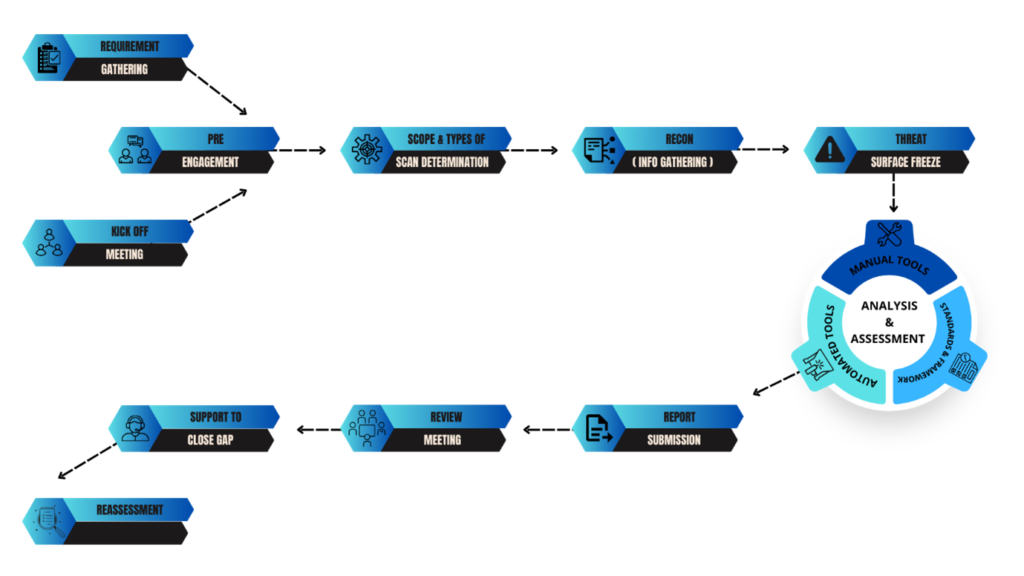
Phase 1. Preparation | Information Gathering
• Meeting with client, scope discussion.
• Determine a complete overview of target systems in scope
• Designate technical & operational people
• Define scan frequency and timing
• Validate inventory details required for assessment
• Preparing recon tools and techniques
• Collect information on systems
• Freezing the detected threat surface area
Phase 2. Test | Analysis
• Use automated tools to discover vulnerabilities.
• Use manual methods to uncover the vulnerabilities which are left over by automated tools.
• Use tools and scripts developed by Valuesec.
• Application of all international standards and procedures into vulnerability findings.
• Valuesec Security specialists manually check for ‘false positives’ in raw data and potential vulnerabilities.
• Using real adversaries and exploits to exploit the identified vulnerabilities.
Phase 3. Report | Explanation
• Writing and reviewing the report
• Present, discuss and review findings together with the client.
Phase 4. Optional Retest | Periodic Follow-up Scans | Delta Reports
• Retest or perform automated periodic vulnerability scans
Our Report Speaks about our Quality
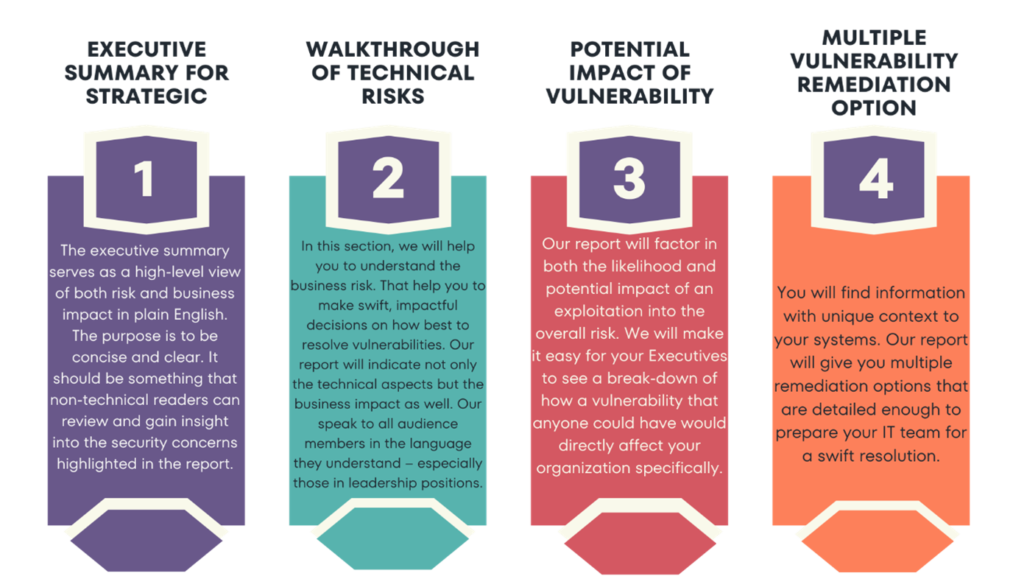
Our USP
- We have a blended approach: Scanning by a highly capable automatic scanner as well as putting more efforts by humans to test manually by using similar tactics used by real hackers.
- Manual penetration testing by cyber experts simulating real hacking
- Uncovers what is left by automatic scanner.
- Find out holes which cannot be simulated by a auto scanner like OTP bypass, headers manipulation, manual sql injections, manual command line injections etc.
- Custom scripts specially designed for your kind of application, which has only motive to break your security.
- A large-scale recon to enlarge the attack surface and that increases the chances of breaking your application from N number of entry points.
- Attempts to break in by using custom and curated tactics, detecting and exploiting command injection flaws (result based, blind, time based etc), usage of custom dictionaries to do brute force, usage of custom and latest xss payloads to break application, custom domain enumeration scripts, domain takeovers, dns transfers etc to name a few

