Offensive Cyber Security
Services
Threat Intel Services
Dark Web Threat Intel and Monitoring
Data brokers and malicious actors continually sell and trade information on the dark web, and security teams alone are often unable to access forums and marketplaces where your data is likely to be found. Dark web monitoring uses both human and artificial intelligence to collect and analyze raw intelligence from across the dark web in real time. Dark web monitoring searches the dark web for information about your organization, including leaked or stolen data, compromised or breached credentials, intellectual property, and other sensitive materials.
We monitor:
- Tor, .onion, .cab and alternative networks;
- Dark web blogs, forums;
- Chatrooms, IRC conversations;
- Black market sites
- Criminal auction sites.
Our dark web monitoring solution can recover the following types of objects and data:
- Stolen Login Credentials
- Compromised Bank Account Information;
- Cloned Credit Card Details;
- Personal Identifiable Information (PII) such as Customer / Employee data;
- Private / Sensitive Documents relating to the business;
- Hacking documents and tools;
- Leaked Source Code;
- Copyright / Trademark infringement;
- Technical Information / Data that could be used to target corporate systems.
Business Benefits
- Data Loss Recovery direct from criminal networks before final fraud event occurs;
- Protect business assets and Intellectual Properties on the deep web;
Bolster existing data loss prevention and anti-fraud counter measures.
Dark Web Threat Intel and Monitoring

OSINT with 0 inputs
The Combination of Internet, Deep and Dark Web is the world’s largest database. If the information exists in real and is legally obtainable, Our OSINT experts will find it.
Valuesec offers market-leading Open-Source Intelligence (OSINT) that provides exceptional insights into your data spread across Internet.
Our OSINT method is powered by technical tools (automated) & people skillsets. Our advanced and matured process allow us to gather and analyse information from a wide range of sources, including:
- Social media
- Blogs
- Chat Sessions
- Blogs
- Dark Web
We offer highly customized OSINT services. You can choose the type of information and depth level you want to receive from our OSINT method. The service can be domain based, keyword based, competitor analysis based. Our OSINT service will always keep you ahead from your competitor.
We also offer more specialised services like Business executives profile monitoring., Business executives face an increasing risk as criminals and hackers target key personnel as a leveraged means of attacking business assets and the corporate network. Cybercriminals can steal Personal Identifiable Information (PII) and private information for the purpose of identity theft, Business Email Compromise (BEC) attacks and spear phishing.
Monitoring Suite employs a variety of services and data correlations, keyword heuristics, including multiple languages, and reverse image-based detection across a variety of platforms. We also have a high degree of expertise in dealing with the removal of offending web content and resolving more complex and sensitive incidents where defamatory or liable cases against individuals occur. Valuesec captures a range of forensic information to assist with law enforcement in applicable cases.
Our Executive Monitoring service will provide protection against:
- Duplicate and fake Social Media accounts, blog and forum content
- Identification of PII posted online and dark web
- Prevent Cyberstalking, online bullying, hacktivism, and defamation
Our Process:
- We prefer a one-day workshop where we evaluate the project scope, identify relevant data and suggest analytics.
- Second part is about Implementation which includes search setup and implementing top of the line analytics (both manual and automated).
- Third and last part is the Operation and Evaluation, with always accurate data delivered.
Penetration Testing
Application Penetration Testing
Our testing methodology goes beyond automated scans and uses highly curated approach to mimic the modern attacks and manipulation of your application.
Doing a penetration testing before go live of any application must be an integral part of any organization IT governance and policies.
Taking a short cut by running a code scanner or crawling on app source code leaves holes in the application for cyber attackers as most code scanning tools just find the low hanging vulnerabilities to fix.
We put ourself in attackers’ shoes and use an ala-carte combination of commercial industry benchmark automated scanners, manual processes, commercial and in-house developed scripts and tools to test the resiliency of application.

External Penetration Testing
Attackers can exploit your web facing platforms – such as billing system, franchise portals, mail login portal, SaaS portals, FTP servers, order booking systems etc. Our external penetration service is designed to test the effectiveness of your network perimeter security controls along with capabilities of target to detect and prevent attacks. Our experts can determine your ability to identify weaknesses in your internet-facing systems.
With a periodic evaluation of cyber resiliency of your external facing systems, devices and apps you can establish trust with partner network, clients and employees about safety of their data.
In today’s cyber market, the key issue is the pull of Ultra Low Cost PenTest services. These ultra-low cost PenTest providers don’t go beyond putting your external IP into the automated scanners and pulling out report. The same report is served as findings of Penetration testing project. This automated scanner approach it not reliable as it skips various things. Our team takes it beyond auto scans and checks all possible ways to exploit the vulnerabilities by reducing the false positives.
Internal Network Penetration Testing
An internal network with high value data is always a big bounty for cyber attackers as they steal, encrypt, delete data to damage your business reputation. The conventional automated scanners don’t really help to uncover the whole threat landscape.
Our pen testers start the Internal pentesting with a standard normal user account in your system and then use that to build the use cases to exploit identified vulnerabilities. We try to take admin control of one or many assets inside your organization and then propagation of attack from one system to another, hence testing the overall network from inside. We test your environment from within with assumption that a threat vector is already inside your environment and mimic all possible action it can do to your assets.
Cloud Penetration Testing
Cloud environments are layered and complex. We understand their intricacies and the methods to exploit them.
If your business utilises one or various cloud services platforms and cloud hosted applications to support your business operations, then of your assets on cloud become one of the top priorities.
Gartner estimates up to 95% of cloud breaches occur due to human errors such as configuration mistakes. Cyber hackers constantly scan the cloud environments to find these security gaps.
Our cloud penetration testing services identify configuration issues and vulnerabilities in your AWS, Azure, or Google Cloud Platform (GCP) infrastructure and guide you to close the security gaps and improve your cloud security posture.
Our cyber security experts combine best-in-class technology and deep cloud expertise to test your cloud environment and its weaknesses against the most common and uncommon attacks. We try to give you a picture of what would happen if a skilled adversary took aim at your protected assets.
We peel back the complex layers of your cloud environment, we put your environment to the test against the same tactics, techniques, and procedures you’re likely to face in a real-world encounter. Extending analysis beyond simple misconfigurations and vulnerabilities, our assessors will uncover a variety of weaknesses and gaps – from unguarded entry points to overprivileged access and vulnerable internal pathways. Cutting through the noise that plagues baseline testing, we focus your security team where it makes the biggest impact.
AWS Pen Testing
Cloud environments have evolved in recent years with more and more companies migrating to cloud infrastructure hosted by providers like Amazon Web Services (AWS). This introduces new vulnerabilities to the infrastructure, and especially with the Shared Responsibility Model, may introduce new risks to a company’s threat model when moving content into the cloud.
Testing and auditing AWS services from a penetration testing perspective requires deep technical knowledge about all available configurations and possible security implications.
We help to uncover issues in IAM, S3 Buckets, Logical Access Control, Databases services and more.
Azure Pen Testing
Penetration testing your Microsoft Azure infrastructure is essential to ensure the security of your cloud, whether you’re migrating to Azure, developing cloud-native applications, using Azure Kubernetes Service (AKS), or performing compliance-related tasks. With the help of Valuesec Expertise, Azure penetration testing can identify high-impact vulnerabilities in your Azure services, including applications that are exposed to the internet.
Azure pen-testing also identifies exposed credentials, improper privileges, and security misconfigurations in your Azure Active Directory integration. These security issues can lead to the compromise of your Azure infrastructure and enable an adversaries to expose sensitive data, take over your Azure resources, or pivot to attack your internal network via Azure environment or permanently destruction of your data.
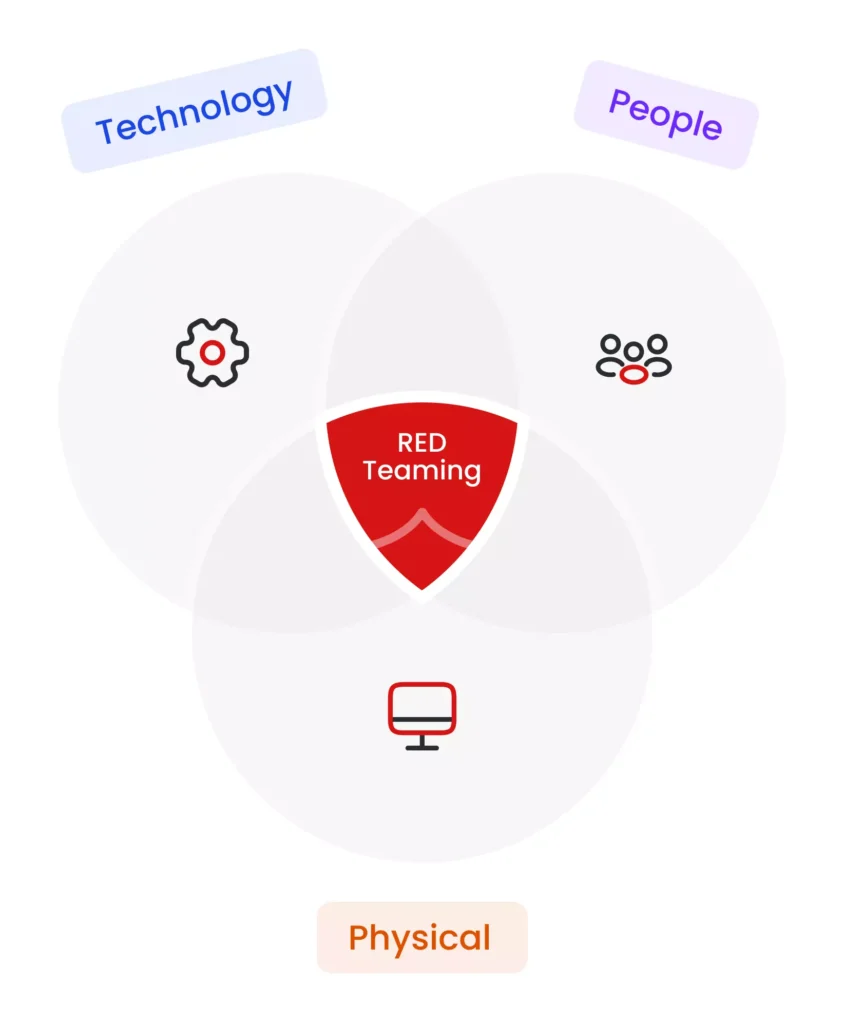
Red Team Engagement
Red Team Exercise is an advance version of Pen Testing. Pen Testing is designed to identify and exploit as many vulnerabilities as possible over a short period of time, while red teaming is a deeper assessment conducted over period of weeks and designed to test an organization’s detection and response capabilities and achieve set objectives such as data exfiltration.
In Summary, the Red team exercise is the simulation of attacks to test and breach the security controls established by the enterprise blue team.
Unlike in Pen Testing where pen-testers keep on doing the testing to find more and more vulnerabilities and exploit them, in Red Teaming we hunt for only one hole good enough to take us deep inside your network and then move freely, doing data manipulations, data exfiltration etc. We rigorously challenge the effectiveness of technology, personnel and process of your enterprise.
Is my Enterprise Ready for Red Teaming Exercise
We recommend to go for Red Team exercise only if you have reached a maturity level in your defence mechanism. In that case, Red Teaming will give maximum ROI on your investment on the project
Red Teaming is the most comprehensive and realistic way to test an organization’s ability to prevent complex cyberattacks. The process utilizes the most advanced tactics, techniques, and procedures (TTPs) from hackers’ arsenals.
During Red Teaming, the client’s security team is purposefully not informed about the engagement. Valuesec’s Red Team simulates the actions of real-life attackers based on specialized threat analysis and hacks the organization in a controlled and effective way. In the long term, the testing helps eliminate gaps in the organization’s information security.
Basic Red Teaming Scenarios
Red Teaming engagement scenarios differ for every client and depend on the goals set. Most often, scenarios include:
- AD (Active Directory) forest taker
- Client data exfiltration
- Access to a top manager’s device
- Intellectual property exfiltration
Our Red Teaming Services helps you to find answers to below questions?
- How effectively do your organization’s existing security measures protect important data?
- Is the organization’s alert and monitoring system configured correctly?
- To what extent is the company’s security team prepared to counter attacks conducted by highly skilled hackers?
- What possibilities become available to attackers within the infrastructure if users or their devices are compromised?
Our approach mirrors the behavior of real-life attackers as closely as possible to not only clearly demonstrate potential scenarios involving hacker attacks but also ensure that information systems are protected effectively.
Social Engineering
You have invested time, resources and energy in training your employees about cyber security threats. It ticks all checkboxes in your internal IT governance body, satisfies all your clients and partners that you have conducted Cyber awareness trainings.
But do you really know how your employees will react at the time of a real cyber-attack? Or if they are equipped well with knowledge that they will spot and report a cyber threat immediately
Today, the data about anyone is available at disposal. People post tonnes of images, updates, video on social media networks, publicly accessible open websites and on various other communication channels. Key information about someone like address, date of birth, dates of various key events in person life is also posted on internet.
Attackers take advantage of these information and launch Social Engineering Attacks to lure your employees to believe them.
In fact Social Engineering Techniques are one of the top techniques used by attackers in executing a full scale cyber attack in enterprises.
Valuesec experts check the awareness of your employees about various tactics used by real attackers. We mimic the various attacks used by modern day attackers to test the resiliency of your employees.
We use below methods to make your employees believe that we are genuine person:
- Simulated phishing emails which may entice to click on a malicious URL, make them to upload document, and have their credentials harvested via fake login pages.
- Vishing phone calls pretending to be someone from your IT Team, finance team or operations team. Creating a sense of urgency and have to tricked into false actions